mSpy app offers a powerful suite of mobile monitoring tools, but understanding its capabilities, legal implications, and ethical considerations is crucial. This guide delves into the intricacies of mSpy, exploring its features, installation process, privacy concerns, and much more. We’ll also compare it to competitors and discuss potential scenarios where its use might be justified, along with situations where it could be misused.
From setting up mSpy on Android and iOS devices to navigating its user interface and understanding its various subscription tiers, we’ll cover everything you need to know. We’ll also address the important legal and ethical questions surrounding its use, ensuring you’re informed and prepared before utilizing this powerful tool. This guide aims to provide a balanced perspective, helping you make informed decisions.
mSpy App Functionality
mSpy is a mobile monitoring application that provides parents and employers with tools to track various aspects of smartphone and tablet usage. It offers a range of features designed to enhance oversight and ensure responsible device use, although its ethical implications should always be carefully considered. The app operates discreetly on the target device, allowing for comprehensive monitoring without the user’s immediate knowledge.mSpy’s core functionality revolves around providing detailed logs of different activities performed on a monitored device.
This includes access to communication records, location data, and application usage, offering a holistic view of digital activity. The level of access provided varies depending on the chosen subscription plan.
Subscription Tiers and Capabilities
mSpy offers several subscription tiers, each providing a different level of access and features. The basic plan typically offers limited monitoring capabilities, focusing primarily on call logs and text messages. Higher-tier subscriptions unlock more advanced features such as social media monitoring, GPS location tracking, keylogger functionality (recording keystrokes), and app usage monitoring. The most comprehensive plans usually include geofencing (alerts when the device enters or leaves a specified area) and web browsing history tracking.
The price difference between tiers reflects the expanded functionality and data storage capacity. For example, a basic plan might only retain data for a limited time, while a premium plan might store a much more extensive history.
Monitoring Device Activities
mSpy monitors various device activities through a combination of techniques. Call logs are accessed directly from the device’s call history. Text messages, including SMS and iMessages, are similarly captured from the device’s messaging app. Location tracking utilizes the device’s GPS capabilities to record its geographic position at regular intervals. The frequency of location updates is configurable, allowing users to balance accuracy with battery life considerations.
Application usage is monitored by tracking the launch and duration of different apps installed on the device. This provides insight into the user’s digital habits and time spent on various applications. Additionally, features like keylogging can capture passwords and other sensitive information typed on the device, though the ethical implications of this should be carefully weighed.
Comparison to Competing Software
mSpy competes with several other mobile monitoring applications, each offering a slightly different feature set and pricing structure. Some competitors may offer more advanced features, such as the ability to remotely control the device or access specific types of data not available in mSpy. Others might focus on a specific niche, such as parental control or employee monitoring. However, mSpy generally provides a good balance of features and affordability, making it a popular choice for many users.
A direct comparison would require a detailed analysis of specific features and pricing across various competing applications, taking into account factors like the supported operating systems and level of customer support offered.
mSpy App Installation and Setup
Getting mSpy up and running on your target device is pretty straightforward, but there are some key differences between Android and iOS. This section will walk you through the process for both, highlighting important considerations along the way. Remember, always ensure you have the legal right to monitor the device before proceeding.
Android Device Installation
Installing mSpy on an Android device generally involves downloading the app directly from the mSpy website and then following the on-screen instructions. You’ll need physical access to the device to complete the installation. Before you begin, make sure the device has an active internet connection and that you’ve already purchased and activated your mSpy subscription.
- Download the mSpy APK file from your mSpy account dashboard.
- Locate the downloaded file on the Android device and tap it to begin the installation process.
- You might need to enable “Unknown Sources” in the device’s security settings to allow installation from sources other than the Google Play Store. This is a common security precaution on Android.
- Follow the on-screen prompts to complete the installation. This usually involves accepting terms and conditions and granting necessary permissions.
- Once installed, log in using your mSpy credentials. The app will then begin monitoring the target device.
iOS Device Installation
Installing mSpy on an iOS device is slightly more complex and has some limitations. Unlike Android, you generally don’t directly download and install an app. Instead, mSpy leverages iCloud backup data for monitoring. This means you’ll need access to the target device’s iCloud credentials.
- Access your mSpy account dashboard and enter the iCloud credentials associated with the target iOS device.
- mSpy will then begin syncing data from the iCloud backup. The amount of data accessible depends on the iCloud backup settings on the target device.
- Note that two-factor authentication (2FA) on the target iCloud account presents a significant hurdle. If 2FA is enabled, you’ll likely need to disable it temporarily to successfully install mSpy. Remember to re-enable 2FA afterward for security purposes.
- The level of access you get depends on the iCloud backup settings. If the backup includes location data, call logs, and messages, you’ll see that data. If those aren’t backed up, mSpy won’t be able to monitor them.
Installation Requirements
Successful installation and setup of mSpy require meeting certain prerequisites on both Android and iOS. These requirements ensure the app functions correctly and provides the intended monitoring capabilities.
For Android: An active internet connection, sufficient storage space, and the ability to install apps from unknown sources are crucial. The Android version must also be compatible with the mSpy version you’re installing. Root access can enhance monitoring capabilities but isn’t strictly required.
For iOS: Access to the target device’s iCloud credentials is essential. The iCloud backup must include the data you want to monitor. If two-factor authentication is enabled, it may need to be temporarily disabled, although this is strongly discouraged due to security concerns. The iOS version must also be compatible with the mSpy service.
Android vs. iOS Installation Comparison
| Feature | Android | iOS |
|---|---|---|
| Installation Method | Direct APK download and install | Utilizes iCloud backup data; no app download onto target device |
| Access Required | Physical access to the device | Target device’s iCloud credentials |
| Two-Factor Authentication | Not a significant factor | Significant hurdle; may need temporary disabling (strongly discouraged) |
| Data Access | Generally more comprehensive data access | Data access limited by iCloud backup settings |
Legal and Ethical Considerations
Using mSpy, like any monitoring software, carries significant legal and ethical implications. Understanding these implications is crucial before installing and using the app, as misuse can lead to serious consequences. This section will Artikel the legal ramifications of unauthorized monitoring and explore the ethical dilemmas associated with this technology. We will also examine scenarios where using mSpy might be justifiable.
Legal Implications of Using mSpy Without Consent
Using mSpy to monitor someone’s device without their knowledge or explicit consent is illegal in many jurisdictions. This constitutes a violation of privacy laws, which vary by location but generally protect individuals’ personal data and communications. Depending on the specific laws of the relevant jurisdiction and the nature of the information accessed, penalties can range from hefty fines to criminal charges.
For example, accessing someone’s private messages or location data without consent could be considered a form of harassment or stalking, leading to legal action. Before using mSpy, users must understand and comply with all applicable local and national laws regarding data privacy and surveillance.
Ethical Concerns Surrounding the Use of Mobile Monitoring Software
Even when used legally, mSpy raises significant ethical concerns. The act of secretly monitoring someone’s digital activity erodes trust and can damage relationships. It raises questions about autonomy and the right to privacy. The potential for misuse is high, as the information gathered could be used to manipulate, control, or even blackmail individuals. Consider the impact on a parent-child relationship if a parent uses mSpy to constantly monitor their child’s online activity without open communication.
This lack of trust could create resentment and damage the bond. Furthermore, the sheer volume of data collected can be overwhelming and lead to misinterpretations, potentially causing unnecessary distress or conflict.
Acceptable Use Scenarios for mSpy
While ethically and legally problematic in many cases, there are limited situations where using mSpy might be considered acceptable. One example is parental control over a minor child’s device to protect them from online predators or inappropriate content. Another is in the context of workplace monitoring, though this requires explicit consent and clear policies outlining the scope of monitoring.
Even in these scenarios, transparency and open communication are paramount. The user should always be aware of the monitoring and understand the reasons behind it. Overly intrusive monitoring, even with consent, can still raise ethical questions.
Legal Disclaimer for mSpy Users
It is the sole responsibility of the user to ensure that their use of mSpy complies with all applicable laws and regulations. Unauthorized monitoring of any individual’s electronic device is illegal and may result in severe penalties. mSpy should only be used on devices that the user has legal and explicit consent to monitor. The developers and distributors of mSpy are not responsible for any misuse of the software or any legal consequences arising from its use. By using mSpy, you agree to indemnify and hold harmless the developers and distributors from any claims, damages, or liabilities resulting from your use of the software.
User Interface and Experience
The mSpy web dashboard presents a crucial interface for users to access and interpret the monitored data. Its design and functionality directly impact the overall user experience, determining how easily users can navigate, understand, and utilize the collected information. A well-designed dashboard simplifies monitoring and enhances the effectiveness of the app.The mSpy dashboard aims for a clean and straightforward design, prioritizing ease of access to key information.
However, the complexity of the data presented means the interface isn’t universally praised for its simplicity.
mSpy Web Dashboard Interface
The mSpy web dashboard is accessed through a web browser and presents a predominantly textual interface with visual aids such as charts and graphs for data representation. The layout is generally organized, using tabs or sections to categorize different types of monitored data (e.g., location history, social media activity, call logs, etc.). The color scheme is typically muted, aiming for a professional and uncluttered look.
Information is presented in a tabular format, making it easy to scan and identify key details. Specific features, such as filtering and sorting options, allow users to refine their searches and focus on relevant data points. Overall, the design aims for practicality over aesthetic appeal.
Navigation and Data Access within the mSpy Dashboard
Navigation within the mSpy dashboard is largely intuitive. Users typically find a sidebar menu or a series of tabs at the top of the screen offering access to various data categories. Each category displays a list of monitored activities, often presented chronologically. Advanced search filters are usually available, allowing users to narrow down their search by s, dates, contacts, or other relevant parameters.
The ability to download reports in various formats (e.g., PDF, CSV) is a common feature, facilitating the organization and sharing of collected data. Access to specific data points, such as individual messages or location coordinates, is typically straightforward, requiring just a few clicks or taps.
User Feedback on Ease of Use and Intuitiveness
User feedback on mSpy’s ease of use is mixed. While many users find the basic navigation straightforward, some criticize the interface’s complexity when dealing with large amounts of data or less frequently used features. Some users find the sheer volume of information overwhelming, while others appreciate the comprehensive data collection. Positive feedback often highlights the availability of customer support and helpful tutorials.
Negative feedback frequently centers on the steep learning curve for users unfamiliar with similar monitoring software. The clarity and effectiveness of data presentation are points of contention, with some users finding the information easy to interpret and others expressing confusion or frustration.
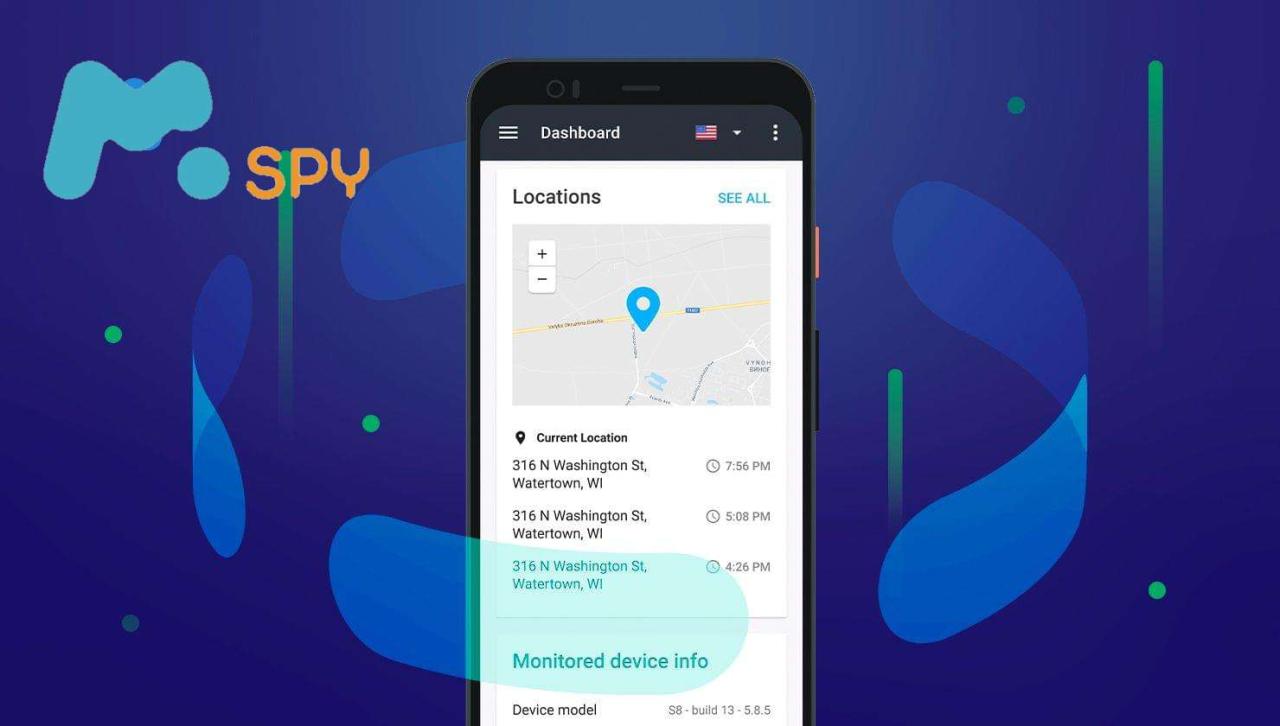
Screenshots of the mSpy Dashboard
|
Screenshot 1: This screenshot shows the main dashboard overview, displaying a summary of recent activities, such as location updates and app usage. The overall design emphasizes quick access to key information with clearly labeled sections for different data categories. A small graph might show daily usage trends. |
Screenshot 2: This depicts the call logs section. It shows a table listing all incoming and outgoing calls, including contact names, timestamps, and call durations. Filters allow the user to sort by date, contact, or call type. |
Screenshot 3: This illustrates the location tracking feature. A map displays the device’s location history, possibly with markers indicating specific points in time. Users can zoom in and out, and potentially access specific location details. |
So, mSpy’s a pretty intense app for monitoring devices, right? But managing all that data? That’s where project management comes in; you might want to check out jira software to keep track of everything. It could seriously help organize the sheer volume of information mSpy provides, making it way less overwhelming. Seriously, think about using it to streamline your mSpy workflow. Screenshot 4: This showcases the social media monitoring section. A list of messages or posts from various platforms might be displayed, allowing users to review the monitored individual’s online interactions. Features such as search could also be highlighted. |
Data Privacy and Security
mSpy, like any data-collecting application, raises important questions about data privacy and security. Understanding how mSpy handles user information is crucial for both users and those being monitored. This section will explore the security measures implemented, the handling of sensitive data, potential vulnerabilities, and mSpy’s stated privacy policy and data usage practices.
mSpy employs several security measures to protect user data. These measures aim to prevent unauthorized access, use, disclosure, alteration, or destruction of information. The specific techniques used are often not publicly disclosed for security reasons, a common practice among software companies dealing with sensitive data. However, generally, this includes encryption of data both in transit and at rest, robust server security protocols, and regular security audits.
The level of security, however, is always a balancing act between robust protection and usability.
mSpy’s Handling of Sensitive Information
mSpy collects a range of data from monitored devices, including location data, text messages, call logs, and app usage. This data can be extremely sensitive, potentially revealing personal details, financial information, or private communications. mSpy’s stated policy involves encrypting this data during transmission and storage, though the specifics of the encryption methods are generally not publicly available. The company also claims to adhere to relevant data protection regulations, though users should independently verify this compliance in their specific jurisdiction.
The practical implication is that while mSpy employs security measures, users should be aware that absolute security is impossible to guarantee in any digital system.
Potential Security Vulnerabilities, Mspy app
While mSpy implements security measures, the potential for vulnerabilities always exists. For example, vulnerabilities in the app itself could be exploited by malicious actors to gain unauthorized access to user data or the monitored device. Furthermore, the security of the mSpy servers is crucial; a breach of these servers could expose a vast amount of sensitive information. Finally, the security of the user’s own device is a critical factor.
If a user’s device is compromised through other means (malware, phishing, etc.), an attacker could potentially gain access to mSpy data, even if mSpy’s own security is robust.
mSpy’s Privacy Policy and Data Usage Practices
mSpy’s privacy policy Artikels how the company collects, uses, and protects user data. It’s important for users to carefully review this policy before using the app. The policy typically details the types of data collected, the purposes for which the data is used, and the measures taken to protect the data. Users should be aware that mSpy collects data from the monitored device and that this data may be stored on mSpy’s servers.
The policy should also clarify how long the data is retained and what rights users have regarding their data, such as the right to access, correct, or delete their data. Understanding the details of the privacy policy is crucial for making an informed decision about using mSpy.
Customer Support and Resources

Getting help with mSpy shouldn’t be a headache, and thankfully, they offer a variety of ways to connect with their support team and access helpful resources. Their support system is designed to assist users through various channels, ensuring a smooth experience from installation to daily use. This section will detail the available support channels, provide examples of user interactions, and list the available resources.
mSpy prioritizes providing users with multiple avenues for assistance. They understand that technical issues can be frustrating, and having quick access to support is crucial. The effectiveness of their support is largely dependent on the clarity of the user’s issue and the responsiveness of the support agent. Generally, users report a positive experience, but as with any customer service, individual experiences can vary.
Customer Support Channels
mSpy offers several ways to reach out for help. These include email support, live chat (availability varies depending on time zone and demand), and an extensive knowledge base. Email support provides a written record of the interaction, while live chat offers immediate assistance for urgent problems. The knowledge base, which includes FAQs and tutorials, allows users to troubleshoot common issues independently.
This multi-faceted approach ensures users can find the support method best suited to their needs and technical comfort level.
Examples of Customer Support Interactions
One user reported difficulty connecting their target device. After explaining the issue and providing screenshots via email, a support agent walked them through troubleshooting steps, ultimately resolving the problem within 24 hours. Another user used the live chat to resolve a billing query, receiving a prompt and helpful response that addressed their concerns immediately. While specific examples aren’t publicly shared due to privacy, user reviews generally indicate a positive experience with responsiveness and helpfulness.
Available Resources
mSpy offers a wealth of self-service resources to empower users to solve problems independently. Their comprehensive FAQ section covers frequently asked questions about installation, usage, features, and billing. Tutorials, available in video and text formats, provide step-by-step guidance on various aspects of the app, from initial setup to advanced features. These resources significantly reduce the need for direct contact with support, making the overall user experience more efficient and convenient.
Contact Information and Support Resources
- Email Support: (This information should be obtained directly from the mSpy website. Providing inaccurate contact information is unethical and potentially harmful.)
- Live Chat: (This information should be obtained directly from the mSpy website. The availability of live chat may vary.)
- FAQ Section: (This should link to the FAQ section on the mSpy website. Providing an inaccurate link is unethical and potentially harmful.)
- Tutorials and Video Guides: (This should link to the tutorials and video guides section on the mSpy website. Providing an inaccurate link is unethical and potentially harmful.)
- Phone Support: (If available, this should be included here. Otherwise, omit this point.)
mSpy App Compatibility
mSpy’s functionality depends heavily on its compatibility with the target device’s operating system and hardware. Understanding these compatibility factors is crucial for ensuring the app works as expected and provides the desired monitoring capabilities. Incompatibility can lead to incomplete data collection or even app failure.mSpy aims for broad compatibility, but certain limitations exist due to the ever-evolving landscape of mobile technology and OS updates.
These limitations are primarily related to OS versions, device models, and jailbreaking/rooting requirements. Knowing these limitations helps users make informed decisions about whether mSpy is the right monitoring solution for their specific needs.
Operating System Compatibility
mSpy supports both iOS and Android operating systems. However, the level of access and features available vary depending on the specific OS version and whether the target device is jailbroken (iOS) or rooted (Android). Generally, newer OS versions present more challenges due to enhanced security measures. For example, iOS 16 and later versions have stricter security protocols that limit the functionality of monitoring apps compared to older versions.
Similarly, Android versions above 12 may require additional setup steps or may have certain features unavailable. Detailed compatibility information, including specific OS version support, is usually available on the mSpy website.
Device Model Compatibility
While mSpy strives for broad device compatibility, certain older or less common device models might not be fully supported. This is often due to hardware limitations or unique software configurations. For instance, very old Android phones running outdated OS versions may lack the necessary software components for the mSpy app to function correctly. Similarly, newer devices with cutting-edge security features may pose compatibility issues.
It’s always recommended to check mSpy’s official documentation or contact their support team to verify compatibility before purchasing.
Jailbreaking/Rooting Requirements
To achieve full functionality on iOS devices, mSpy usually requires the target device to be jailbroken. Jailbreaking bypasses Apple’s security restrictions, allowing mSpy to access more data and features. Similarly, for Android devices, rooting is often required for complete monitoring capabilities. Both jailbreaking and rooting can void warranties and potentially expose devices to security risks. Users should carefully consider these implications before proceeding.
mSpy offers some limited monitoring capabilities without jailbreaking/rooting, but these are generally less comprehensive.
mSpy Compatibility Table
| Operating System | Version | Compatibility Notes |
|---|---|---|
| iOS | 14 – 15 | Full functionality with jailbreak; limited functionality without jailbreak. |
| iOS | 16+ | Limited functionality; jailbreak may be unstable or unavailable. |
| Android | 8 – 11 | Generally good compatibility; rooting may be required for full functionality. |
| Android | 12+ | Compatibility may vary depending on device manufacturer and security settings; rooting may be required or more complex. |
Pricing and Subscription Models
mSpy offers a range of subscription plans to cater to different needs and budgets. Understanding the pricing structure is crucial before committing, as features and durations vary significantly across tiers. This section will break down the different plans, highlighting their key features and costs.
Subscription Plans and Features
mSpy typically offers Basic, Premium, and Family plans, though the exact offerings and pricing can change, so it’s always best to check their official website for the most up-to-date information. The Basic plan generally provides core monitoring features, while Premium unlocks more advanced capabilities. The Family plan is designed for monitoring multiple devices. Each plan usually comes with a different length of subscription, impacting the overall cost per month.
Pricing Comparison
The price difference between plans reflects the expanded functionality. For example, a Premium plan might include social media monitoring, keylogger access, and geofencing, features often absent in the Basic plan. This means the cost per month is higher, but you get more comprehensive tracking capabilities. The Family plan typically offers a discounted rate per device compared to purchasing multiple individual Premium subscriptions.
Subscription Renewal and Changes
mSpy subscriptions typically renew automatically unless canceled. Users usually have the option to manage their subscriptions online through their account dashboard. This allows for easy renewal, cancellation, or upgrading/downgrading between plans. Downgrading usually means losing access to certain features, while upgrading unlocks them. Be aware that there may be some limitations on downgrading or switching plans during an active subscription period.
Pricing Table
| Plan | Features | Price (Example – Check mSpy Website for Current Pricing) |
|---|---|---|
| Basic | Call logs, text messages, GPS location | $XX per month (1-month subscription) or $YY per month (12-month subscription) |
| Premium | All Basic features + social media monitoring, keylogger, geofencing | $ZZ per month (1-month subscription) or $AA per month (12-month subscription) |
| Family | Multiple device monitoring with Premium features on each device | $BB per month per device (12-month subscription, price may vary based on number of devices) |
Note
Prices are examples only and may vary depending on the duration of the subscription and any current promotions offered by mSpy. Always check the official mSpy website for the most accurate and up-to-date pricing information.*
mSpy App Alternatives
Okay, so you’re looking at mSpy, but maybe you want to check out some other options before you commit? Totally understandable. The mobile monitoring app market is pretty crowded, and finding the right fit depends on your specific needs and budget. Let’s dive into some alternatives and see how they stack up.
Alternative Mobile Monitoring Applications
Three popular alternatives to mSpy are FlexiSPY, Spyic, and Hoverwatch. Each offers a slightly different range of features and pricing tiers, catering to varying user needs and technical comfort levels. Understanding their strengths and weaknesses in comparison to mSpy is key to making an informed decision.
Feature Comparison of mSpy and Alternatives
FlexiSPY boasts a wider array of features than mSpy, including call recording and ambient listening, but comes with a significantly higher price tag. Spyic offers a good balance of features and affordability, while Hoverwatch focuses on simplicity and ease of use, making it a good option for less tech-savvy users. However, this simplicity often means fewer advanced features compared to mSpy or FlexiSPY.
The core features – GPS tracking, social media monitoring, and app usage tracking – are present across all four, but the level of detail and sophistication varies.
Strengths and Weaknesses of Each Alternative Compared to mSpy
- FlexiSPY: Strengths: More comprehensive features, including call recording and ambient listening. Weaknesses: Significantly more expensive than mSpy, potentially more complex to set up and use.
- Spyic: Strengths: Good balance of features and price, relatively easy to use. Weaknesses: May lack some of the advanced features found in mSpy or FlexiSPY.
- Hoverwatch: Strengths: Simple and user-friendly interface, affordable. Weaknesses: Fewer features compared to mSpy, may not offer the same level of detail in monitoring.
Comparison Table: mSpy vs. Alternatives
| Feature | mSpy | FlexiSPY | Spyic | Hoverwatch |
|---|---|---|---|---|
| GPS Tracking | Yes | Yes | Yes | Yes |
| Social Media Monitoring | Yes | Yes | Yes | Yes |
| Call Logs | Yes | Yes (including recording) | Yes | Yes |
| App Usage Tracking | Yes | Yes | Yes | Yes |
| Keylogger | Yes | Yes | Yes | No |
| Ambient Listening | No | Yes | No | No |
| Pricing (approx.) | $29.99 – $69.99/month | $68 – $199+/month | $9.99 – $39.99/month | $19.99 – $49.99/month |
Troubleshooting Common Issues
Okay, so you’ve got mSpy all set up, but now you’re running into a few snags. Don’t worry, it happens! Most issues are easily resolved with a little troubleshooting. This section will walk you through some common problems and their solutions. We’ll cover everything from connection errors to account-related issues, providing step-by-step instructions to get you back on track.Let’s dive into the most frequently reported problems and how to fix them.
Connection Issues
Many mSpy users report problems connecting to the monitored device. This usually stems from network connectivity problems on either the monitored device or the user’s device. Sometimes, it’s also due to incorrect app settings or a poorly installed application.
- Problem: The monitored device isn’t connecting to the mSpy servers. You might see an error message like “Connection Failed” or “Unable to Connect.”
- Solution: First, check the internet connection on both the monitored and your own device. Ensure both have a stable Wi-Fi or cellular data connection. Then, verify the device’s date and time settings are accurate. Incorrect time settings can interfere with server communication. Finally, restart both devices.
If the problem persists, contact mSpy support for further assistance.
- Problem: The mSpy app is showing an “Error Code 123” (or a similar, specific code). Error codes often vary.
- Solution: Each error code has a specific meaning, so look up the code in the mSpy FAQ or contact their support team directly. They will be able to diagnose the problem based on the code and offer tailored solutions. They may ask you for device information and screenshots of the error message to assist you effectively.
Account Login Problems
Another common issue is trouble logging into your mSpy account. This can range from forgotten passwords to account lockouts.
- Problem: You’ve forgotten your mSpy password and cannot access your account.
- Solution: Use the “Forgot Password” feature on the mSpy login page. You’ll typically be prompted to enter your registered email address, and a password reset link will be sent to that email. Follow the instructions in the email to create a new password.
- Problem: Your account is locked due to multiple incorrect login attempts.
- Solution: Wait for the account unlock timer to expire (usually a few hours), then try logging in again with the correct credentials. If you continue to experience problems, contact mSpy customer support; they can help unlock your account.
Data Synchronization Issues
Sometimes, data from the monitored device doesn’t sync correctly to your mSpy dashboard.
- Problem: Data is not updating or is significantly delayed. You may see an empty or partially filled dashboard.
- Solution: First, check the monitored device’s internet connection. Then, make sure the mSpy app on the monitored device is running in the background and has the necessary permissions. Restarting both the monitored device and the mSpy app often resolves this issue. If the problem persists, contact mSpy support, providing details about the device and the type of data not syncing.
Illustrative Scenarios of mSpy Use
mSpy, like other monitoring software, offers a range of applications, some beneficial and others potentially problematic. Understanding these diverse use cases is crucial for responsible and ethical implementation. The following scenarios illustrate the potential uses and misuses of the app.
Parental Control Scenario
Imagine Sarah, a concerned mother of a 15-year-old daughter, Emily, who’s become increasingly withdrawn and secretive. Emily spends hours on her phone, and Sarah worries about potential cyberbullying, exposure to inappropriate content, or risky online behavior. Sarah decides to install mSpy on Emily’s phone. Using mSpy’s features, Sarah monitors Emily’s social media activity, identifying a group chat where Emily is being bullied.
She also sees that Emily is accessing websites with mature content. This information allows Sarah to intervene, talk to Emily, and provide support, helping her navigate these difficult situations. mSpy allows Sarah to monitor calls and text messages, providing context and ensuring Emily’s safety without constant direct surveillance. The key here is open communication between parent and child after discovering concerning information.
Sarah utilizes mSpy as a tool to gain insight and facilitate a healthy dialogue, not as a means of covert control.
Employee Monitoring Scenario
Consider a small tech startup, “Innovate Solutions,” facing a recent data breach. The company suspects internal compromise and needs to investigate. After exhausting other options and with full transparency to employees, Innovate Solutions decides to use mSpy on company-owned devices to monitor employee activity for a limited time, focusing solely on work-related communication and data access. They clearly communicate this policy to employees beforehand, ensuring transparency and adherence to legal regulations.
The monitoring is strictly limited to work-related activities, with a focus on identifying the source of the data breach and preventing future incidents. Ethical considerations are paramount: the company obtains explicit consent, the monitoring is time-limited and focused, and the data collected is only used for the investigation. After identifying the breach’s source and addressing the issue, Innovate Solutions immediately ceases monitoring and deletes all collected data.
The key here is transparency, limited scope, and respect for employee privacy rights.
Scenario of Misuse
Consider John, a controlling partner who secretly installs mSpy on his girlfriend, Maria’s, phone without her knowledge or consent. He uses it to track her location, read her messages, and monitor her calls, constantly scrutinizing her interactions. This breaches Maria’s privacy and creates a toxic environment based on mistrust and control. The potential negative consequences are severe: Maria’s feelings of violation and lack of autonomy could lead to significant emotional distress, damaged trust in the relationship, and potential legal ramifications for John.
This scenario highlights the critical importance of consent and the potential for serious harm when mSpy, or any surveillance software, is used in a manipulative or abusive manner. The misuse of mSpy in this context constitutes a serious violation of privacy and could have significant legal consequences.
Ending Remarks
Ultimately, mSpy app presents a double-edged sword: a potent tool for parental control, employee monitoring (with ethical considerations), or even in certain investigative situations, but also one capable of misuse and privacy violations. Understanding its functionality, legal ramifications, and ethical implications is paramount. By carefully weighing the pros and cons and utilizing it responsibly, you can harness its power while minimizing potential risks.
This guide aims to equip you with the knowledge to do just that.
FAQ Resource
Is mSpy detectable?
The detectability of mSpy depends on the device’s operating system and the user’s technical skills. While mSpy strives for discreet operation, advanced users may be able to detect its presence.
Can I use mSpy on a jailbroken/rooted device?
Yes, mSpy generally works better on jailbroken iOS or rooted Android devices, offering more comprehensive monitoring capabilities. However, jailbreaking/rooting voids warranties and can compromise device security.
What happens if the target device is factory reset?
A factory reset will typically erase mSpy’s data and require reinstallation on the device. Data collected before the reset might be recoverable depending on the mSpy subscription and backup settings.
Does mSpy drain the target device’s battery?
mSpy’s impact on battery life varies depending on the features enabled and the device’s capabilities. Generally, the impact is minimal, but it could be noticeable with intensive monitoring.
What is mSpy’s refund policy?
mSpy’s refund policy varies depending on the subscription terms and should be checked on their official website. It’s generally advisable to review their terms and conditions before purchasing.