PDF Password Remover: Ever been locked out of a crucial PDF? We’ve all been there. This isn’t just about forgotten passwords; it’s about the technology behind unlocking them, the legal and ethical considerations, and the ever-evolving cat-and-mouse game between password protection and removal tools. From understanding the different types of PDF passwords to exploring the security risks and legal implications of bypassing them, we’ll unravel the complexities of PDF password removal.
This exploration delves into the history of PDF password remover software, examining its popularity and the various platforms where you can find these tools. We’ll compare free and paid options, analyze their functionalities and features, and even discuss the technical nitty-gritty of how they work. Beyond the technical aspects, we’ll also tackle the ethical dilemmas, legal ramifications, and user experience considerations associated with using these tools.
Ultimately, we aim to provide a comprehensive overview of PDF password removers, empowering you with knowledge to make informed decisions.
Popularity and Trends of PDF Password Removers
PDF password remover software has become increasingly prevalent as the use of PDFs for sensitive documents has grown. Its popularity is directly tied to the need for accessing restricted files, whether for personal use, professional projects, or archival purposes. The evolution of this software reflects both technological advancements and shifting user needs.
Historical Usage Patterns of PDF Password Remover Software
Early adoption of PDF password removers was largely driven by individual users needing access to password-protected documents. As PDF became the de facto standard for document sharing and storage, the demand for such software naturally increased. The initial tools were often basic and sometimes unreliable, focusing primarily on brute-force attacks against simpler passwords. The rise of more sophisticated encryption methods in PDFs led to the development of more advanced cracking techniques incorporated into newer software.
The increase in online document sharing and cloud storage further fueled the growth, as users needed tools to access documents from various sources and devices. This trend continues to this day, with the addition of mobile accessibility becoming a significant factor.
Top Platforms for Finding PDF Password Remover Tools
Three dominant platforms consistently feature a large selection of PDF password remover tools: software download websites (such as Download.com or Softonic), online app stores (like the Google Play Store and Apple App Store for mobile applications), and search engines (primarily Google). Software download sites often offer user reviews and comparisons, while app stores provide ratings and security information.
Search engines allow users to directly search for specific tools or compare options based on their individual needs and reviews. The relative popularity of these platforms reflects the diverse ways users discover and acquire software.
Market Share of Free vs. Paid PDF Password Remover Software
The market for PDF password removers is segmented between free and paid options. Free software often offers limited functionality, such as removing simple passwords or handling only specific PDF versions. Paid software, in contrast, typically provides broader functionality, supports more advanced encryption methods, and often includes features like batch processing and enhanced security. While the precise market share is difficult to definitively quantify, it’s safe to say that a significant portion of the market utilizes free software for basic needs, while users requiring more robust features or higher security tend to opt for paid versions.
The free market often relies on advertising revenue or limited functionality to compensate for the lack of direct payment.
Timeline of PDF Password Remover Technology Evolution
A simplified timeline illustrates the evolution:
| Year (Approximate) | Key Development |
|---|---|
| Early 2000s | Emergence of basic, often unreliable, password cracking tools primarily targeting simple passwords. |
| Mid-2000s | Improved algorithms and increased sophistication in handling more complex encryption methods. Increased focus on user-friendliness. |
| Late 2000s – Present | Integration with cloud storage services, mobile device compatibility, batch processing capabilities, and enhanced security features become common. Sophisticated tools capable of handling 128-bit and 256-bit encryption emerge. |
Functionality and Features of PDF Password Removers
PDF password removers are software applications designed to circumvent security measures implemented on PDF documents. Understanding their functionality requires a grasp of the different types of passwords used and the techniques employed to crack them. This section will delve into the mechanics of these tools, comparing their performance and highlighting key features.
PDF Password Types
PDF documents can be protected by two main types of passwords: user passwords and owner passwords. A user password restricts access to the document’s content; you can’t view or print the PDF without the correct password. An owner password, on the other hand, controls the permissions associated with the document. This means the owner password controls actions like editing, printing, copying, and modifying the document’s security settings.
Sometimes, a PDF might only have one type of password, while other times it might have both.
Methods Used to Bypass PDF Protection
PDF password removers employ various methods to remove or bypass these passwords. These methods range from brute-force attacks (trying numerous password combinations) to dictionary attacks (trying common passwords and variations) and more sophisticated techniques that exploit vulnerabilities in the PDF encryption algorithms. Some advanced tools might utilize a combination of these approaches for increased effectiveness. The specific methods used vary depending on the software and the complexity of the password.
Brute-force attacks, for instance, are time-consuming and computationally expensive, especially for complex passwords, but are effective against simple passwords. Dictionary attacks are faster but less effective if the password isn’t in the dictionary.
Performance Comparison Across File Sizes and Complexities
The performance of a PDF password remover varies considerably depending on factors such as the password’s complexity, the size of the PDF file, and the software’s algorithm efficiency. Larger files with complex, long passwords naturally take longer to process. A simple four-digit password might be cracked almost instantly, while a long, complex alphanumeric password could take hours or even days, depending on the remover’s capabilities and the processing power of the computer.
Furthermore, the encryption algorithm used in the PDF also affects processing time; some algorithms are more resistant to cracking than others. For example, a 10MB PDF with a simple password might be processed in seconds, whereas a 100MB PDF with a complex password could take significantly longer.
Comparison of Popular PDF Password Remover Tools
Below is a comparison table of three popular PDF password remover tools. Note that the performance figures are estimates and can vary based on the specific hardware and software configurations.
| Feature | Tool A | Tool B | Tool C |
|---|---|---|---|
| Price (USD) | $29.99 | $49.99 | Free (with limitations) |
| Speed (Estimated for average PDF) | Fast (seconds to minutes) | Moderate (minutes to hours) | Slow (minutes to hours, or may fail) |
| Supported PDF Versions | 1.1 – 2.0 | 1.0 – 2.0 | 1.0 – 1.7 |
| Operating Systems | Windows, macOS, Linux | Windows, macOS | Windows only |
Security Implications of PDF Password Removers
Using PDF password removers presents a complex ethical and security landscape. While they offer convenience for accessing locked documents, their use raises significant concerns regarding copyright infringement and the potential for malware exposure. Understanding these implications is crucial for responsible and safe usage.
Ethical Considerations of Using PDF Password Removers on Copyrighted Materials
Employing a PDF password remover to access copyrighted material without authorization is a clear violation of copyright law. This is akin to stealing a physical book from a library – the digital lock doesn’t change the fundamental illegality of accessing material you don’t have permission to view. The consequences can range from civil lawsuits demanding significant financial compensation to criminal prosecution, depending on the severity and scale of the infringement.
Remember, even if the document is password-protected, it’s still protected by copyright unless you have explicit permission from the copyright holder.
Potential Risks Associated with Unreliable PDF Password Remover Software
Downloading PDF password remover software from untrusted sources dramatically increases your risk of malware infection. Many malicious actors disguise malware as legitimate software, often incorporating features that mimic the functionality of a password remover. Once installed, this malware can steal your personal data, including passwords, financial information, and sensitive documents. It can also compromise your system’s security, making it vulnerable to further attacks.
Data breaches resulting from such infections can have severe consequences, impacting both your personal life and professional reputation. For instance, a compromised system could lead to identity theft or the exposure of confidential business information.
Best Practices for Using PDF Password Removers Securely
To mitigate risks, only download PDF password remover software from reputable sources like well-known software vendors with established reputations. Always verify the software’s digital signature to ensure its authenticity. Before installing any software, thoroughly read user reviews and security analyses. Consider using a virtual machine (VM) to run the software, isolating it from your primary operating system and preventing potential malware from spreading.
Finally, keep your antivirus software up-to-date and scan any downloaded files before execution.
Examples of Vulnerabilities Exploitable by Malicious Actors
A compromised PDF password remover could contain malicious code that logs keystrokes, allowing attackers to steal passwords or other sensitive information entered by the user. It might also include backdoors that grant remote access to the user’s system, enabling the attacker to install additional malware or steal data. Furthermore, a malicious PDF password remover could inject malicious code into the unlocked PDF itself, allowing attackers to deploy exploits when the document is opened.
For example, a seemingly innocuous document could contain a hidden script that downloads ransomware onto the user’s system. This illustrates how seemingly benign software can become a vector for serious attacks.
Legal Aspects of PDF Password Removers
Navigating the legal landscape surrounding PDF password removers can be tricky. The legality of using such software hinges heavily on the context of its use and the nature of the protected PDF. Simply put, removing a password without authorization is generally illegal, while removing a password from a document you own or have explicit permission to access is perfectly fine.
Password Removal and Copyright Infringement
Removing a password from a copyrighted PDF without permission constitutes copyright infringement. This is because the password protects access to the copyrighted work. Bypassing that protection and accessing the content without authorization is a violation of the copyright holder’s exclusive rights to control the distribution and use of their work. The penalties for copyright infringement can vary depending on factors such as the nature of the work, the extent of the infringement, and the jurisdiction.
So, you’ve got a PDF with a password, right? That’s a total drag. But once you crack that, you might need a solid program to edit it, which is why grabbing a copy of Microsoft Office via microsoft office 365 download is a good idea. Then you can easily edit that unlocked PDF using Word, making sure you have all the tools you need to handle those pesky password-protected files.
These penalties could include hefty fines and legal action by the copyright holder.
Legally Permissible Scenarios for PDF Password Removal
There are situations where removing a password from a PDF is perfectly legal. For example, if you are the owner of the PDF and simply forgot the password, removing it to regain access is perfectly acceptable. Similarly, if you have explicit permission from the copyright holder to remove the password, you are acting within the bounds of the law.
Another example is if the password protects access to a document in the public domain; since the work is not protected by copyright, removing the password does not constitute an infringement. Finally, removing a password for the purpose of forensic analysis or in response to a court order, acting within the confines of the law, is also generally acceptable.
Fair Use and PDF Password Removal
The concept of “fair use” is a complex legal doctrine that allows limited use of copyrighted material without permission from the copyright holder. It’s important to understand that fair use is a defense against copyright infringement, not a blanket permission to use copyrighted material in any way. The application of fair use to password removal is highly fact-specific and depends on several factors, including the purpose and character of the use, the nature of the copyrighted work, the amount and substantiality of the portion used, and the effect of the use upon the potential market for or value of the copyrighted work.
For example, removing a password to quote a small portion of a copyrighted research paper for a scholarly review might be considered fair use, while removing a password to copy and distribute the entire work would certainly not be.
International Legal Considerations
The laws governing the use of PDF password remover software vary significantly across countries. A comprehensive list of every country’s specific laws is beyond the scope of this discussion, but it is crucial to remember that the legal implications of password removal are jurisdiction-specific. What might be permissible in one country could be illegal in another. Before using a PDF password remover, it is advisable to research the relevant laws in the jurisdiction where you are located and where the copyrighted material originates.
Ignoring these legal differences can result in significant legal repercussions.
User Experience and Interface Design
The user experience (UX) of a PDF password remover is crucial for its success. A clunky, confusing interface can frustrate even tech-savvy users, leading to negative reviews and ultimately, a lack of adoption. Conversely, a well-designed interface can make the process of removing a password quick, easy, and even enjoyable, leading to positive word-of-mouth and increased market share.
This section will examine typical interface elements, compare the UX of several popular tools, and offer recommendations for improvement.
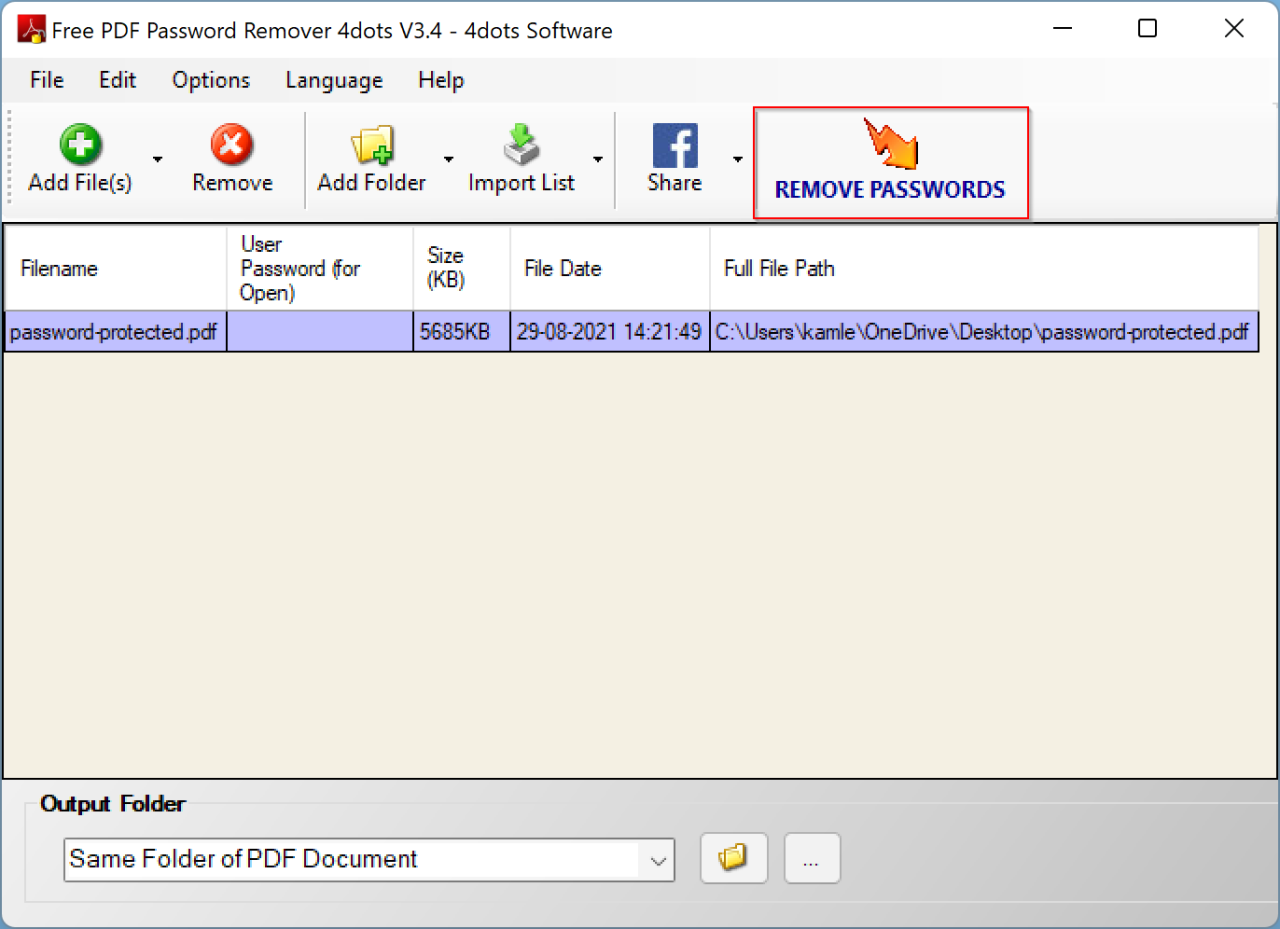
Most PDF password removers share a common set of interface elements. Users typically begin by selecting the PDF file they wish to unlock, either through a file browser window or drag-and-drop functionality. Once the file is selected, the software displays the password field (if applicable) and an option to initiate the password removal process. Progress bars often indicate the software’s status, and upon successful completion, users are presented with an option to save the unlocked PDF.
Error messages, if any, are usually displayed prominently to help users troubleshoot potential issues. Advanced features, such as batch processing or options for specific password types, might be available through additional settings menus.
Typical User Interface Elements in PDF Password Remover Software
PDF password remover software typically employs a straightforward interface. Common elements include a file selection button or drag-and-drop area, a password input field (if required), a “Remove Password” or similar button to initiate the process, a progress bar to visually represent the process’s status, and an area to specify the output location for the decrypted PDF. Many programs also incorporate options for handling multiple files at once (batch processing) and detailed settings menus for advanced users.
A clear, concise help section is also a vital element for assisting users who encounter difficulties.
Comparison of User-Friendliness Across Three PDF Password Remover Tools
Let’s consider three hypothetical tools – “EasyUnlock,” “SecurePDF,” and “PasswordPro.” EasyUnlock boasts an exceptionally clean and intuitive interface. The file selection is straightforward, the password field (if necessary) is clearly labeled, and the process is initiated with a single, prominently placed button. SecurePDF, while functional, presents a slightly more cluttered interface with numerous settings options, potentially overwhelming novice users.
PasswordPro, on the other hand, features a minimalist design, but its lack of clear instructions or progress indicators can leave users feeling uncertain about the process’s status. EasyUnlock provides the most user-friendly experience due to its simple, uncluttered design and straightforward workflow.
Recommendations for Improving the User Experience of PDF Password Remover Applications
Several improvements could enhance the user experience of PDF password remover applications. Firstly, clear and concise instructions should be readily available, possibly through tooltips or a comprehensive help section. Secondly, the use of visual cues, such as progress bars and clear status messages, is crucial to keep users informed throughout the process. Thirdly, error messages should be informative and provide actionable steps for users to resolve the issues.
Finally, a streamlined workflow with minimal steps is crucial for a positive user experience. Consider implementing drag-and-drop functionality and intuitive button placement to minimize the number of clicks required to complete the password removal process.
User Flow Diagram for Removing a PDF Password Using “EasyUnlock”
Imagine a user flow diagram for EasyUnlock. The diagram would begin with the user opening the EasyUnlock application. The next step would be selecting the password-protected PDF file, either by browsing to its location or using drag-and-drop. If the PDF is password-protected, the user would be prompted to enter the password. After entering the password (or bypassing it if the software supports password cracking), the user clicks the “Remove Password” button.
A progress bar would then display the process’s status. Upon completion, the user would be presented with an option to save the unlocked PDF to a chosen location. The entire process should be visually represented in a simple, linear flow chart, making it easy for users to understand the steps involved.
Technical Aspects of PDF Password Removal

PDF password removal isn’t magic; it relies on a combination of clever algorithms and brute force, often exploiting weaknesses in the PDF format itself. Understanding these techniques helps clarify both the capabilities and limitations of password recovery tools.
Underlying Algorithms and Techniques
Password cracking for PDFs often involves attacking the encryption algorithms used to protect the document. Many PDFs employ AES (Advanced Encryption Standard) encryption, a robust algorithm resistant to simple attacks. However, vulnerabilities can exist in how the encryption is implemented within the PDF file itself. Some tools exploit weaknesses in the PDF file structure to bypass the encryption entirely, rather than directly attacking the password itself.
Others leverage dictionary attacks, trying common passwords or variations thereof, or brute-force attacks, systematically testing every possible password combination. The success rate depends heavily on the password’s complexity and the resources available to the attacker. A weak, easily guessable password will be cracked far faster than a strong, randomly generated one.
Brute-Force Password Recovery
A brute-force attack systematically tries every possible password combination within a given character set and length. For example, a four-character password using only lowercase letters (26 possibilities per character) has 26 4 = 456,976 possible combinations. A tool performing a brute-force attack will generate and test each of these possibilities until it finds the correct password, or exhausts all possibilities.
The time required increases exponentially with password length and character set complexity (adding uppercase letters, numbers, and symbols dramatically expands the search space). Specialized hardware, like GPUs (Graphics Processing Units), can significantly accelerate this process by performing many password tests concurrently. However, even with such hardware, cracking a long, complex password remains computationally infeasible for most users.
Comparison of Password Cracking Methods
Different methods have varying effectiveness. Dictionary attacks are relatively fast but only succeed if the password is common or easily guessable. Brute-force attacks are exhaustive but can be incredibly time-consuming, especially for strong passwords. Exploiting vulnerabilities in the PDF file structure can sometimes bypass the password entirely, but these vulnerabilities are often patched quickly by software developers.
The choice of method often depends on the password’s strength and the attacker’s resources. A simple password might yield to a dictionary attack, while a complex one might require a resource-intensive brute-force attack or a targeted vulnerability exploit.
Removing a PDF Password Using a Command-Line Tool
While many graphical user interface (GUI) tools exist, some command-line tools can also handle PDF password removal. These tools often rely on the same underlying techniques as GUI applications, but offer a more streamlined and automated process. The specific steps vary depending on the chosen tool, but generally involve specifying the target PDF file and initiating the password removal process.
The tool might then attempt various cracking methods, displaying progress and results to the user in the command-line interface. For instance, a tool might display the number of passwords tested, any potential matches found, and the overall time elapsed. Note that successful removal depends on the password’s complexity and the tool’s capabilities. Some tools might offer different algorithms or options for customizing the attack, such as specifying character sets or word lists.
However, ethical considerations should always be prioritized; using such tools on files you don’t own is illegal.
Alternative Methods for Accessing Password-Protected PDFs
Sometimes, wrestling with a PDF password just isn’t worth it. There are other ways to get access, and sometimes these are better options than using a password remover, especially considering the potential security and legal risks. Let’s explore some alternatives.
Contacting the PDF Owner
This is often the simplest and most legitimate approach. If you know who created the PDF and why it’s password-protected, reaching out directly is the best way to get access. A simple email explaining your need for the document can often resolve the issue quickly.
Utilizing Cloud Storage Services
Cloud services like Google Drive, Dropbox, or OneDrive sometimes offer features for collaborative document editing and sharing. If the PDF is stored on a shared cloud drive, you might have access permissions already granted. Check the sharing settings. If not, you might be able to request access from the file owner.
Alternative File Formats
Sometimes the information you need might exist in another, less protected format. Check for alternative versions of the document (e.g., a Word document or a plain text file). This might save you the hassle of dealing with a password altogether.
Comparison of Alternative Methods
Here’s a quick comparison of the pros and cons of each method:
| Method | Pros | Cons |
|---|---|---|
| Contacting the Owner | Legitimate, efficient, often resolves issues quickly. | Requires knowing the owner, may involve delays in response. |
| Cloud Storage Services | Convenient if the file is already shared, avoids password cracking. | Requires access permissions, relies on the owner’s cooperation and cloud storage usage. |
| Alternative File Formats | Avoids password issues, efficient if alternative formats exist. | Alternative formats may not always be available, might lack formatting or specific features of the original PDF. |
Situations Where Alternative Methods Are Preferable
Using a password remover carries potential legal and security risks. Alternative methods are preferable when:
- You don’t have the technical expertise to safely use a password remover.
- You’re unsure of the legal implications of accessing the PDF without permission.
- The PDF contains sensitive information, and using a password remover could compromise security.
- A simpler, more direct approach (like contacting the owner) is readily available.
Decision Tree for Accessing Password-Protected PDFs
This decision tree guides you through choosing the best method:
Do you know the owner of the PDF?
Yes -> Contact the owner
No -> Is the PDF stored on a cloud service you have access to?
Yes -> Check cloud sharing settings
No -> Does an alternative file format exist?
Yes -> Use the alternative format
No -> Consider other options, carefully weighing the legal and security implications before using a password remover.
Cost and Pricing Models of PDF Password Removers
The cost of removing PDF passwords varies wildly, depending on the software’s features, the vendor’s business model, and the user’s specific needs. Understanding these pricing models is crucial for making an informed decision. Let’s break down the common approaches and what influences their price points.
PDF password remover software typically employs one of three main pricing models: free, freemium, or subscription-based. Free options often come with limitations, such as restricted functionality or watermarks on the output. Freemium models offer a basic free version alongside a paid version with advanced features. Subscription-based services charge recurring fees for access to the software’s full capabilities. The choice depends heavily on how often you need to remove passwords and the complexity of the PDFs you handle.
Factors Influencing the Cost of PDF Password Remover Software
Several factors contribute to the price of PDF password remover software. The complexity of the algorithms used to crack passwords plays a significant role; software capable of handling stronger encryption methods will naturally be more expensive. The level of support offered, including customer service responsiveness and the availability of documentation, also impacts the price. Additional features like batch processing, integration with other software, and advanced editing capabilities all add to the overall cost.
Finally, the vendor’s brand recognition and market position can influence pricing. Established players with a strong reputation might command higher prices than newer entrants.
Comparison of Pricing Plans for Popular PDF Password Removers
The following table compares the pricing plans of three hypothetical, but representative, PDF password removers: “PassCracker Pro,” “PDFUnlocker,” and “SecurePDF.” Remember that pricing is subject to change, and these are examples to illustrate the range of options available.
| Feature | PassCracker Pro | PDFUnlocker | SecurePDF |
|---|---|---|---|
| Pricing Model | One-time purchase | Freemium (free with limitations, paid for full features) | Subscription (monthly/annual) |
| Basic Price | $29.99 | Free (limited features); $19.99 (full features) | $9.99/month; $99.99/year |
| Batch Processing | Included | Paid version only | Included in all plans |
| Technical Support | Email support | Limited online resources; paid support available | 24/7 chat and email support |
| Watermark Removal | Included | Paid version only | Included in all plans |
Value Proposition of Paid versus Free PDF Password Remover Tools
Paid PDF password remover tools often provide a superior user experience, more robust features, and better support compared to their free counterparts. Free tools frequently have limitations, such as processing speed, file size restrictions, or the inclusion of watermarks on the decrypted PDFs. For infrequent use or simple PDFs, a free tool might suffice. However, for frequent use, complex documents, or professional needs, the added features and reliability of paid software are often worth the investment.
Consider the frequency of use and the importance of data integrity when making your decision. A paid option often provides peace of mind and efficiency gains that outweigh the cost.
Future Trends in PDF Password Removal Technology
The field of PDF password removal is constantly evolving, driven by advancements in cryptography and the ever-present cat-and-mouse game between security measures and those seeking to circumvent them. Predicting the future is inherently uncertain, but based on current trends, we can anticipate significant shifts in both the techniques used to remove passwords and the challenges faced by developers and users alike.The increasing sophistication of encryption algorithms and the rise of quantum computing pose significant challenges to existing PDF password removal methods.
Current methods often rely on brute-force attacks or exploiting vulnerabilities in older PDF standards. However, these approaches will likely become increasingly ineffective as PDF security improves.
Advancements in Password Cracking Techniques
As encryption methods become more robust, password crackers will need to adapt. We can expect to see a greater reliance on advanced techniques such as AI-powered password guessing, leveraging machine learning to identify patterns and weaknesses in passwords more efficiently than brute-force methods. This might involve analyzing password dictionaries, incorporating contextual information, and even using neural networks to predict likely password choices.
For example, a future tool might analyze metadata embedded within a PDF to infer potential passwords related to the document’s content or author.
Emerging Challenges in PDF Security, Pdf password remover
The proliferation of sophisticated encryption methods, coupled with the growing power of quantum computing, presents a significant challenge. Quantum computers, once sufficiently developed, could potentially break many currently secure encryption algorithms, rendering current PDF password removal techniques obsolete and requiring the development of entirely new, quantum-resistant cryptographic methods. Furthermore, the increasing integration of PDFs into various online platforms and cloud storage systems creates new vulnerabilities that could be exploited by attackers.
Predictions for PDF Password Remover Software
We anticipate the development of more specialized and efficient password removal tools. These tools might incorporate advanced algorithms, heuristics, and machine learning techniques to target specific vulnerabilities in different PDF versions or encryption methods. For example, a future tool might dynamically analyze the PDF structure and encryption type before selecting the optimal cracking strategy. This would improve efficiency and reduce the time required for password removal.
We also predict an increase in the use of cloud-based password removal services, offering greater accessibility and scalability.
Impact of Advancements in Cryptography
The development of post-quantum cryptography (PQC) will significantly impact PDF password removal technology. PQC algorithms are designed to resist attacks from both classical and quantum computers. As PQC becomes more widely adopted, existing password removal techniques will become less effective, necessitating the development of entirely new methods capable of breaking these more robust encryption schemes. This could involve exploring novel approaches to cryptanalysis or focusing on exploiting potential weaknesses in the implementation of PQC algorithms within PDF software.
The transition to PQC will likely be a gradual process, with a period of coexistence between legacy and new cryptographic methods. This will create a complex landscape for PDF password removal technology, requiring constant adaptation and innovation.
Last Recap
Unlocking the secrets of PDF password removers reveals a fascinating intersection of technology, ethics, and law. While these tools offer convenient solutions for accessing locked documents, understanding their capabilities, limitations, and potential risks is paramount. From choosing the right tool to navigating the legal landscape, informed usage ensures both efficiency and responsible digital citizenship. Remember, always consider the ethical and legal implications before attempting to remove a password from a PDF that isn’t yours.
Hopefully, this deep dive has equipped you with the knowledge to approach PDF password removal responsibly and effectively.
FAQ Compilation
Can PDF password removers remove all types of PDF passwords?
No, some highly secure PDFs might resist even the most powerful removers. The effectiveness depends on the encryption method used and the complexity of the password.
Are all PDF password removers safe to use?
Definitely not. Many contain malware or are designed to steal your data. Stick to reputable sources and read reviews before downloading any software.
What if I forget the password to my own PDF?
Some PDF creators offer password recovery options. Otherwise, a password remover might work, but it depends on the password’s complexity. Contacting the software provider might also be an option.
Is it illegal to use a PDF password remover on a copyrighted PDF?
Generally, yes, unless you have permission from the copyright holder or the use falls under “fair use” exceptions (which are very narrowly defined). It’s a serious legal gray area.
How do I choose a reliable PDF password remover?
Look for software with positive reviews, strong security features, and a transparent privacy policy. Avoid anything that looks too good to be true or comes from an untrustworthy source.